Recall
Grub is a piece of software that gets executed every time you boot your GNU/Linux machine, just before the init of your operating system.
Thanks to GRUB, you can choose which OS or Kernel to boot from at startup. You also are able to send informations directly to the kernel when it launchs.
Grub is localed in a clear partition that is different from your main OS one, which means that when your system is encrypted, there is no way to access it locally, UNLESS in the case of a bruteforce
(I excluded the possibility of leaving your system unlocked...)
We find here the importance of encrypting your partitions, so that you don’t get exposed to a situation of stealing/data manipulation and/or privilage escalation locally from the physical machine.
Tricks | Privesc from GRUB
Here I am, invited to a friend’s house! He tells me he uses GNU/Linux and sells himself to be safe. He goes away taking care to turn off his machine because he doesn’t trust me, let’s show him that it is possible to pop a root shell in an instant since his hard disk is not encrypted
Let’s turn on his machine!
We land on its GRUB, let’s not press enter but the "E" key (editing function)
Let’s go down a little bit until we find the line "linux /boot/vmlinuz[...] ro quiet"
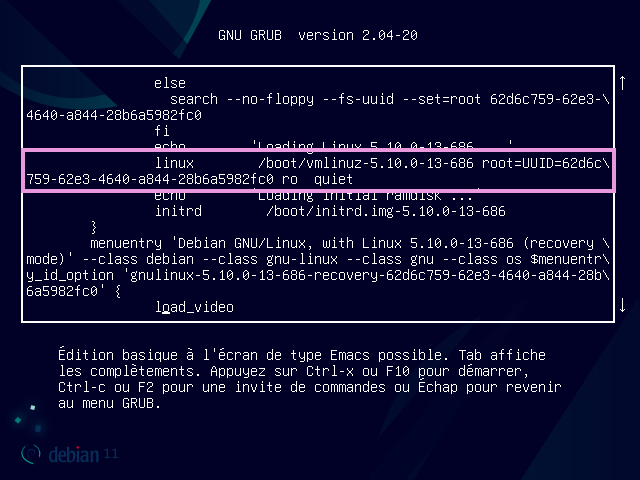
Don't be surprised: you can't setxkbmap, you'll have to make do with qwerty.
Here we will edit the ro by rw instead, ro means Read-Only and rw Read-Write. This allows us to change the privileges of the user to let him write and not only read.
We will then add init=/bin/bash to our line: init is a start-up kernel parameter taking any executable/binary as parameter /bin/bash refers to your bash shell contained in /bin/bash
More documentation about kernel parameters is availible here
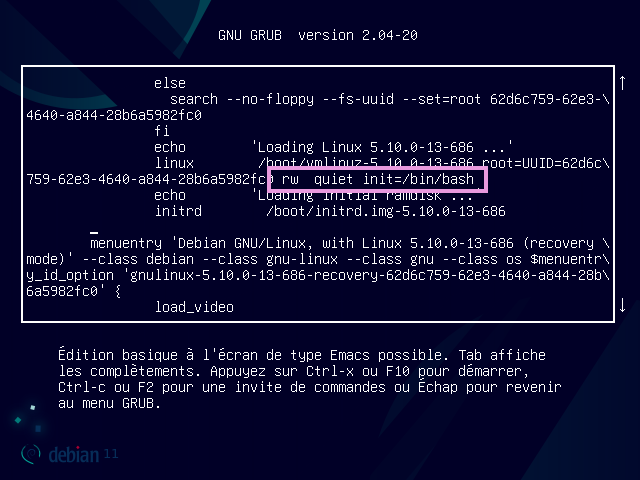
Press F10, then it’s done (ᵔᵕᵔ)/
We find ourselves on a root shell with the ability to edit as desired, it’s beautiful isn’t it? :D
We can now classically change the root password with passwd root.
Kernel panick | How to avoid it
Stay here, it’s not over!
You can’t get out of this environment in the classical way, try an exit and the machine will go into kernel panick
What you see is a screen of a kernel panick that I was able to experiment on my own machine some time ago after making an init kernel change
The cleanest and safest way to get out of here in order to reboot is to use poweroff -f.
Thanks for reading c:
Special thank | Crystal (๑˘ ³˘)⠀~♡
Special thank to Crystal, she translated this article. <3